Taming the Shadow: A Comprehensive Guide to Managing Unsanctioned IT
Have you ever wondered if your company's computer systems are like a well-organized library, or more like a messy closet where things are hidden? Sometimes, employees use software, apps, and devices that the IT department doesn't know about. This is called "shadow IT," and it can cause some problems. Let's explore what shadow IT is, why it happens, and how to manage it effectively.
Understanding the Landscape of Shadow IT
The Rise of Shadow IT
Shadow IT isn't new, but it's become more common because of a few things:
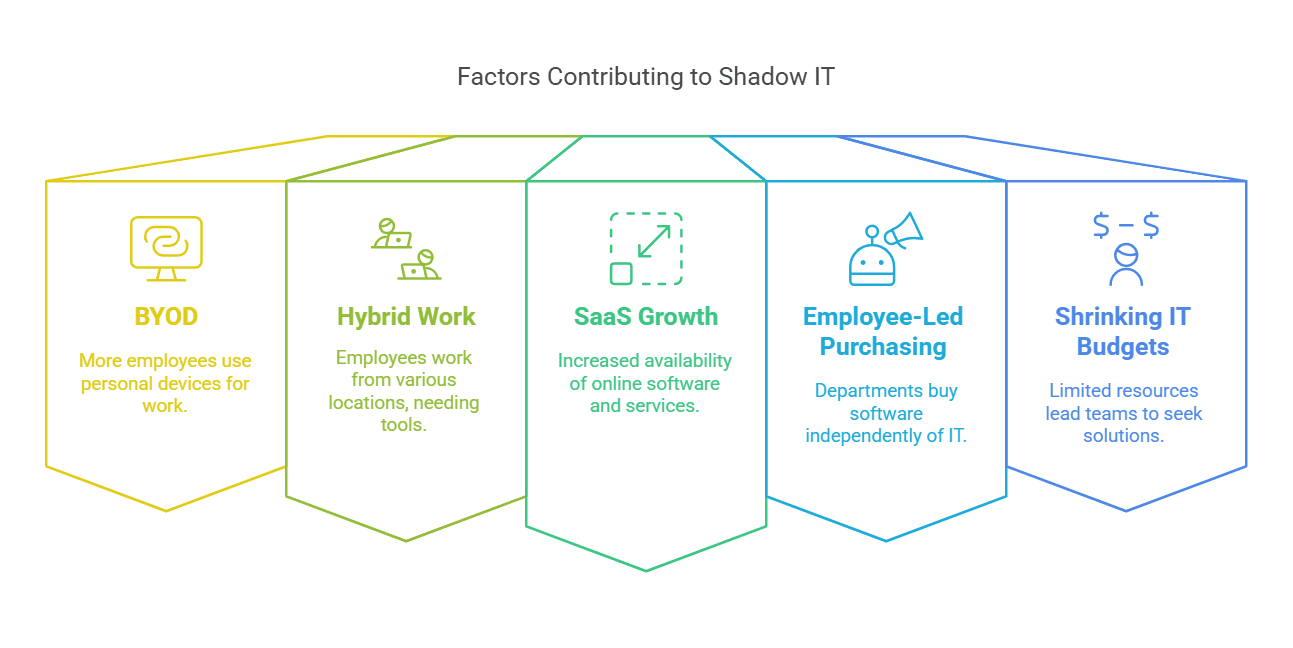
- BYOD (Bring Your Own Device): More people use their personal phones and laptops for work.
- Hybrid Work: Many employees now work from home or different locations, needing different tools.
- SaaS Growth: There are many online software and services that are easy to buy and use.
- Employee-Led Purchasing: Departments often buy their own software without involving IT.
- Shrinking IT Budgets: When IT departments have less money and fewer people, business teams may start looking for their own solutions.
These factors have made it easier for employees to use technology that isn't managed by the IT department.
Why Employees Turn to Shadow IT
Employees often use shadow IT for good reasons:
- Efficiency and Convenience: They need tools that help them work faster and easier.
- Frustration with IT: Sometimes, getting new software through IT takes too long.
- Personalization: They want tools that fit their specific needs and preferences.
- Lack of Awareness: They might not know about the tools that the company already has, or how to ask for new ones.
- User Experience: When the tools provided by IT don't do what employees need, they may look for alternatives.
For example:
- An employee might build their own coding setup if the company laptop isn’t fast enough.
- An employee who is used to Macs may use one even if the company issues Windows devices.
These examples show that shadow IT often comes from a desire to be more productive and efficient.
Sources of Shadow IT
Shadow IT can come in different forms:
- Employee Purchases: Software and apps bought by employees using their own credit cards and then expensed.
- Unsanctioned Cloud Services: Online tools and AI platforms that employees use without IT approval.
- Personal Devices (BYOD): Using personal laptops, smartphones, and tablets for work.
- Redundant Applications: Apps that do the same job as other apps already in use by the company.
The Double-Edged Sword: Benefits and Risks
Potential Benefits of Shadow IT
Shadow IT isn't always bad. It can have some benefits:
- Driving Innovation: Teams can try out new technologies to find better ways of working.
- Employee Empowerment: When employees choose their tools, they often become more satisfied and productive.
- IT Efficiency: IT can focus on bigger projects if they don't have to manage every little tool that employees are using.
The Risks of Unmanaged Shadow IT
However, shadow IT also comes with risks if it's not managed well:
Increased Costs:
- Duplicated Apps: Paying for the same software multiple times.
- Budgeting Problems: It's hard to know how much is being spent on software.
- Missed Savings: Not being able to negotiate better prices for software.
- Hidden Expenses: Software purchases are sometimes misclassified in expense reports and go unnoticed.
Security Vulnerabilities:
- Unvetted Apps: Software that hasn't been checked for security issues.
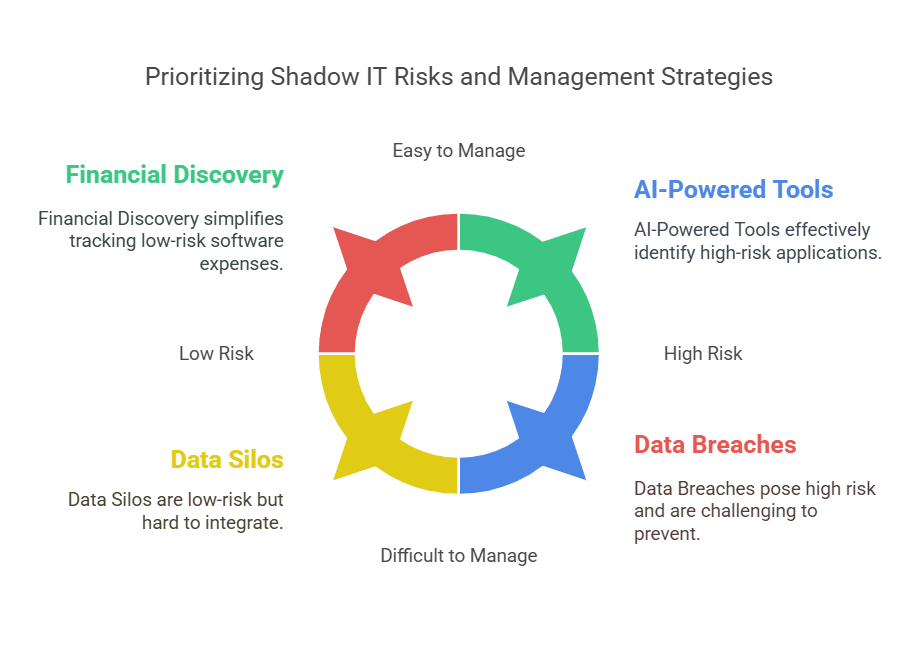
- Data Breaches: Increased risk of cyberattacks and data leaks.
- Hidden Software: Shadow IT can be hidden from enterprise security systems.
Compliance Issues:
- Regulations: Breaking rules like GDPR and HIPAA unintentionally.
- Data Governance: It becomes difficult to keep company data safe and secure.
Operational Inefficiencies:
- Lack of Integration: Shadow IT applications may not work well with other company systems.
- Data Silos: Information gets scattered across different apps and is hard to find.
- Lack of Visibility: IT doesn't know which apps are being used and how.
- Sustainability Issues: Shadow IT solutions may fall apart when the employee who created them leaves.
Strategies for Effective Shadow IT Management
Gaining Visibility: The First Step
The first step in managing shadow IT is to find out what's being used. This is where SaaS Management Platforms (SMPs) come in.
- Financial Discovery: Tracking expenses to find out where money is being spent on software is very important.
- Limitations of Spreadsheets: Tracking everything manually in spreadsheets can be time-consuming and error-prone.
- Discovery Tools:
- SSO (Single Sign-On): Good for tracking managed tools, but not for everything.
- Web Browser Plugins: Easy for employees to bypass.
- CASB (Cloud Access Security Broker): Doesn't always track data from personal devices.
- Financial Analysis: Can be helpful, but prone to human errors.
- AI-Powered Tools: Use machine learning to identify both known and unknown applications.
Establishing a Clear Governance Framework
It’s important to have clear rules about how software is bought and used:
- Centralized Governance: Moving from departments buying their own software to having IT manage the process.
- "Freedom within a Framework": Allowing employees to choose tools, while still keeping IT in control.
- Standardized Software Catalogs: Helping employees find approved tools easily.
- Clear Policies: Having rules about what IT allows and the consequences for breaking the rules.
Creating Dynamic Policies
Instead of just blocking apps completely, it can be more effective to create policies that control how data is used. For example:
- Restrict uploads to personal accounts on high-risk apps.
- Use browser isolation to safely access high-risk websites.
Technology Solutions to Manage Shadow IT
Anti-Shadow IT Technologies
- Cloud Access Security Brokers (CASB): Monitor how cloud apps are being used and enforce security policies.
- Endpoint Detection and Response (EDR): Detect unusual activity and lock access to unauthorized devices.
- IT Configuration Management Software: Automatically discover and flag unapproved software.
- Zero Trust Network Access (ZTNA): Limit access to company data and systems only to approved devices and apps.
- User Access Management Tools: Limit administrator access to company systems.
Pro-Shadow IT Technologies
- Mobile Device Management (MDM): Manage personal devices by creating secure workspaces on them.
- Enterprise Sandbox Environments: Allow users and IT to test new software in a safe space.
- Virtual Desktop Environments: Allow access to apps without transferring data to the user's device.
The Cultural and Organizational Shift
The Role of Leadership
- Leaders should promote innovation while maintaining rules.
- Open communication between leadership, IT, and employees is crucial.
Employee Awareness and Training
- Provide training to help employees understand the risks.
- Encourage a culture where everyone takes responsibility for security.
Building a Dedicated Team
- Create a central team that manages shadow IT.
- The shadow IT team and department representatives can work together to manage tools effectively.
Measuring Success and ROI
- Key Metrics:
- Reduced spending on shadow IT.
- Improved security scores.
- Increased satisfaction with IT tools.
- More adoption of approved software.
The Future of Shadow IT
- Emerging Trends:
- Edge Computing, IoT, and Remote Work will all influence shadow IT.
- AI tools can pose a specific risk as they may be used without oversight.
Conclusion
Managing shadow IT is about finding the right balance. By gaining visibility, setting clear rules, and working with employees, you can manage shadow IT successfully.
Take a proactive approach to shadow IT and start with AlphaSaaS to gain control and ensure compliance within your organization.

Aisha Javed
Aisha, a thinker, a reader, a doodler and quite an observer. She enjoys meaningful conversations and believes that food is the ultimate source of happiness. She is passionate about learning new things and is drawn to picking up new hobbies, although she isn’t very good at sticking to them.